Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another persons personal data in some way that involves fraud or deception typically for economic gain. Identity theft page 1 identity theft.
To prevent such terrible things from developing, secure yourself using the fine protection service. Once volunteers recognize that financial info is not necessary for volunteer service, many relax immediately.
Data Breaches And The Long Term Risk Of Credit Card Fraud
A situation of worry passard c.

No fuss identity theft methods considered. However when considering high tech methods of identity theft theres not much that you can do. What are identity theft and identity fraud. For example if the risk of identity theft is low your program might focus on how to respond if you are notified say by a customer or a law enforcement officer that someones identity was misused at your business.
154 million americans were victims of identity theft in 2016 according to javelin researchid theft has been among the top consumer complaints with the federal trade commission ftc for the last 17 years and ranked as the 1 consumer complaint from 2000 to 2015. The person whose identity has been assumed may suffer adverse consequences especially if they are held responsible for the perpetrators actions. Identity crimes most common schemes types of identity crimes identity theft begins when someone takes your personally identifiable information such as your name social security number date of birth your mothers maiden name and your address to use it without your knowledge or permission for their personal financial gain.
Identity theft has become big business for criminals. Low tech methods such as dumpster diving and telephone scams are easier to fight against because they take advantage of a victims personal habits. With the use of computer viruses hacking and zer day attacks thieves can get personal information from your computer.
Identity theft is the deliberate use of someone elses identity usually as a method to gain a financial advantage or obtain credit and other benefits in the other persons name and perhaps to the other persons disadvantage or loss. When we consider how identity theft happens the various scams and other common methods of identity theft tend to fall into one of two categories. 14 identity theft methods used by criminals.
Credit card fraud was the leading method for identity theft the ftc reported with new accounts accounting for 24 of the complaints and old accounts accounting for 12 of the crimes. Sensitive information is gathered through low tech methods of physically. Dean saint leo university joshua buck saint leo university pierce dean saint leo university abstract despite enormous advances in society and technology millions of people have their identities stolen.
Identity theft is when someone fraudulently uses your personal information such as your name date of birth social security number and address for their financial gainthese uses might include to obtain credit get a loan open a bank or a credit card account or obtain an id. If identity theft isnt a big risk in your business complying with the rule is simple and straightforward.

How To Protect Yourself From Identity Theft Axel Medium
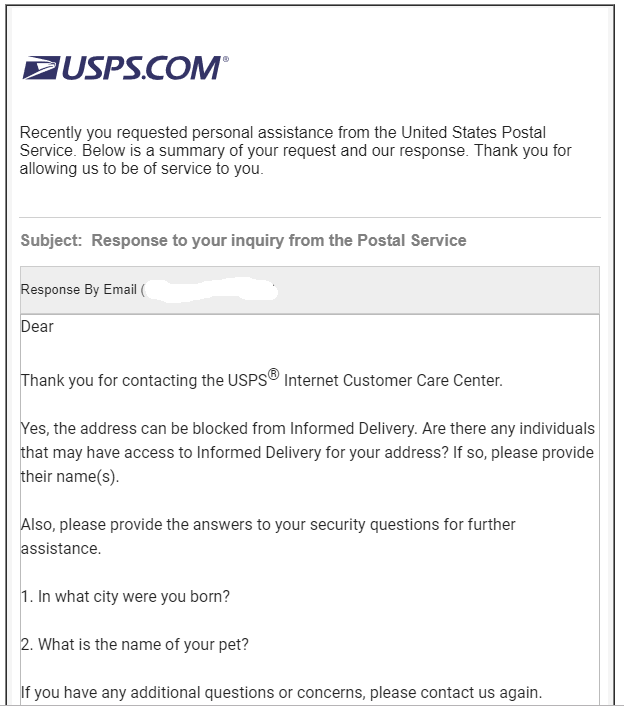
U S Secret Service Warns Id Thieves Are Abusing Usps S Mail

Home Idnext

Payments Wufoo







0 comments:
Post a Comment