It is very important to look at an intensive look of ones billing statement. Your personal and financial information would be the vital puzzle pieces that hackers need to take over your identity.

44788 The Error System Xml Xmlexception Root Element Is Missing

Data Management Insights Sas

Fraud Waste And Abuse In Entitlement Programs Deloitte Insights
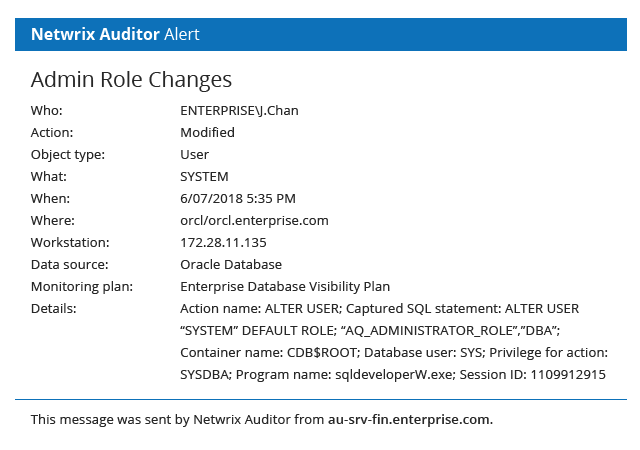
Oracle Database Auditing With Netwrix Auditor

2018 S Top Telecom Fraud Threats
So, I think, I should say, to guard yourself and those youre keen on, at any time. You never know, the hackers are smart enough to accumulate the specified information within you using several tricky means. They notice that it may be a few years ahead with their crime is uncovered by some time it can be found itll be difficult to track them down.











0 comments:
Post a Comment